Cypherix®’s comprehensive corporate security solution provides encryption based security implementation for data at rest, using the existing hardware and Windows infrastructure of the enterprise. The secure vault can be moved to any other Windows machine with the Cryptainer Enterprise install.
It addresses vital security issues such as intellectual property protection, access control, sharing over intranet and internet, and hierarchical dissemination of information with our integrated admin password manager.
* Instant electronic delivery!!
Buy NowDownload Fully functional trial version of Cryptainer Enterprise
Try Now| Stops | Installation | Maintenance | |
|---|---|---|---|
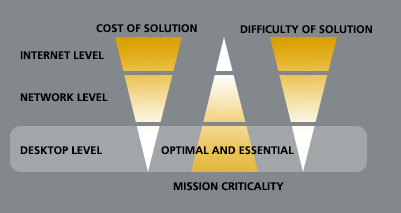
| Internet Level Security | Hackers | Weeks | 24/7 |
| Network Level Security | Hackers, Competition | Months | 24/7 |
| Desktop Level Security | Competition, Insiders | Hours | None |
Costs involved in securing data
Cryptainer Enterprise, like all Cypherix products uses the cryptographically secure Blowfish strong encryption scheme operating at a bit strength of 448 bits. Cryptainer Enterprise has all the functionality of Cryptainer, plus an additional administrative module for password recovery. With well over 7 million Cypherix users, Cryptainer has a proven user base and stable software. The end-user interface is identical to that of Cypherix products, the award winning, easy-to-use encryption software. Cryptainer Enterprise ensures your privacy by keeping your data private and secure on your PC as well as removable storage. Specially tailored to meet the growing security and privacy needs of the corporate user, Cryptainer Enterprise combines the ease of use and simple drag-and-drop operations with strong encryption.
All modules are based on a secure implementation of the blowfish strong encryption algorithm at key strength of 448 bit. The Cryptainer Enterprise based solution has the following primary security features:
It is our belief that it is crucial to the adaptation of any security scheme that there be no deviation in the end user's patterns of normal computing. With this in mind, End user components in the scheme have been specially designed to ensure maximum utility and simplicity of use.
Cryptainer Enterprise works with all 32 bit as well as 64 bit versions of Microsoft Windows (Windows XP, Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows 11). It encrypts on all file systems such as FAT, FAT12, FAT32, NTFS or NTFS with EFS.
Powerful command line processing available for encrypting/decrypting at the dos prompt. Group a series of encryption and decryption commands in a single or multiple batch files.
Corporate users can maintain control, despite individual end users’ freedom to set independent passwords, without administrative intervention. In case an employee leaves or inadvertently encrypts vital data, it is possible for the corporation to recover such data, if they so deem necessary.
The Cryptainer Administrative Module provides corporate users with single point control and monitoring of the distributed vaults without introducing any of the weaknesses inherent in the underlying operating systems. This ensures the integrity of your data, and at the same time gives you flexibility and overall control. You have the freedom to implement your company security policies without changing any underlying software.